There’s been a lot of emphasis placed on the effectiveness of a track and trace system in the fight against Covid-19. It’s hard to disagree that a system which will help stop the virus is a good thing, but there are already signs that the companies behind the system aren’t doing the best job with personal data.
So what steps do you need to take to keep yourself safe? What do you need to watch out for? Is taking part in the system really a good idea at all? Here’s our considered advice about how best to protect yourself.
What is the new NHS test and trace system?
The Government needs a way to keep Covid-19 under control and one of the most effective ways to do that – as demonstrated by the experience of other countries – is an effective track and trace programme. Having information about who has the virus and where they are should allow a broader lifting of lockdown, with more localised restrictions imposed to control local outbreaks.
The idea is that when someone tests positive, a team of tracers tracks down people they have been in contact with during the time they were infectious and those people are also asked to isolate to stop the virus spreading further.
The UK’s track and trace system was launched in England and Scotland last week. It’s different to the app being developed to identify if a person has been in close proximity to someone later diagnosed with Covid-19, which is still being trialled on the Isle of White.
There have been a few hiccups along the way, not least the breach of data protection rules when one of the companies recruiting tracers shared their email addresses with others being recruited, leading to an apology.
If we can’t trust the companies involved with the system to look after their own employees’ data, can we really trust them to look after the personal and sometimes sensitive data of the general public? It’s not off to a good start, and public confidence is an absolute necessity if a track and trace system is to work.
What data and cyber security issues does the track and trace system present?
If you have a positive Covid-19 test you will be asked for lots of personal data, as well as data and contact information for people you have been in contact with.
If you have been in close contact with someone who later has a positive test for Covid-19 you may be contacted by phone, email or text message to ask you to self-isolate and you may need to give the NHS Test and Trace system your personal details.
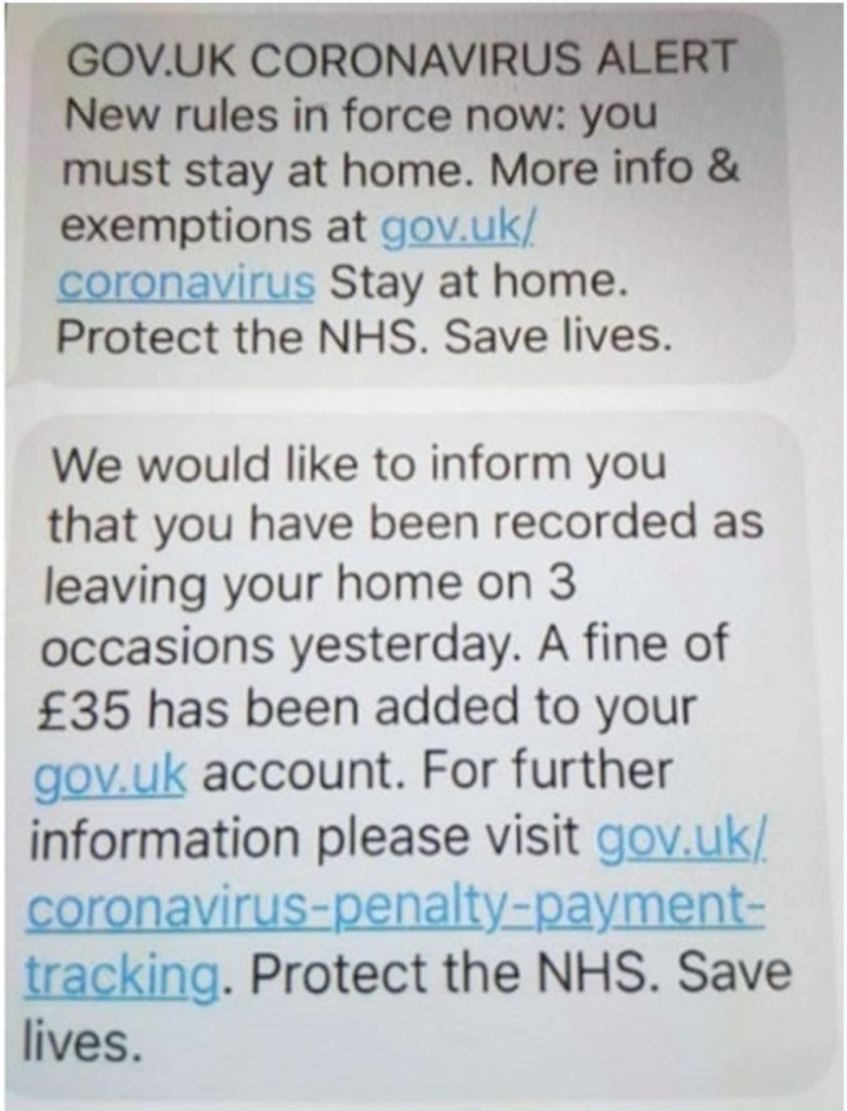
But how would you know a call asking you to self-isolate was genuine? Dr Jenny Harries, the Deputy Chief Medical Officer for England, did little to allay fears about how people would know the contact was legitimate when the only reason she gave for someone to believe a call from the Test and Trace operation was genuine was that it would be very evident the callers are “professionally trained individuals”. So scammers can’t sound professional then? Not much of a reassurance.
The NHS website states: “Text messages will come from the NHS. Calls with come from 0300 0135000.” But we know it’s not too difficult to make texts look like they come from a certain organisation, and unless you save the number in your phone, a call from a similar number could be misconstrued as genuine.
Another security issue is in the length of time people’s data will be kept. Data of people with a positive Covid-19 test will be stored for 20 years. If you do not have a positive Covid-19 test your data will be stored for five years. A range of companies are involved in the storage of the data, so we’re relying on them to have the right processes and procedures in place to keep it safe.
Our best advice about engaging with NHS Test and Trace
The usual message about scam calls, texts and emails applies here. Be on your guard. Do not click through to any links in emails or texts. Do not give out personal data over the phone.
If you are asked to provide data, go directly to the official Test and Trace website rather than following links you are given.
Here’s what the official guidelines about the service say will happen:
- call you from 0300 013 5000 (But this can be spoofed)
- send you text messages from ‘NHS’ (But this can be spoofed)
- ask for your full name and date of birth to confirm your identity, and postcode to offer support while self-isolating
- ask if you are experiencing any coronavirus symptoms
- provide advice on what you must do as you have been in contact with someone who has tested positive for coronavirus
And here’s what the guidelines say contact tracers will never:
- ask you to dial a premium rate number to speak to us (for example, those starting 09 or 087)
- ask you to make any form of payment or purchase a product of any kind
- ask for any details about your bank account
- ask for your social media identities or login details, or those of your contacts
- ask you for any passwords or PINs, or ask you to set up any passwords or PINs over the phone
- disclose any of your personal or medical information to your contacts
- provide medical advice on the treatment of any potential coronavirus symptoms
- ask you to download any software to your PC or ask you to hand over control of your PC, smartphone or tablet to anyone else
- ask you to access any website that does not belong to the government or NHS
Be suspicious if anyone asks you for this kind of information. If you aren’t sure, use the principles of the Take 5 initiative, and stop to think before acting or giving out any information.
Ultimately, it’s your decision about whether you engage with the NHS Test and Trace programme. There are some very real risks, but many – although not all – can be managed if you take sensible precautions.